This article will analyze the above issues based on the ECMP operation principle and explore how to optimize the use of ECMP.
Equal-cost multipath routing
ECMP Implementation Process
Step 1: Selection of HASH Factor
|
Traffic load balancing mode
|
HASH Factor
|
|
SRC-MAC
|
Source IP address (SlP)
|
|
DST-MAC
|
|
|
SRC-DST-MAC
|
|
|
SRC-MAC
|
|
|
SRC-IP
|
Source and destination IP address (SlP + DlP)
|
|
DST-IP
|
|
|
SRC-DST-IP
|
Source and destination IP address, L4 port source and destination (SIP + DIP + SP + DP)
|
|
SRC-DST-IP-L4PORT
|
Enhanced mode, extracting message fields based on load balancing profile, can define and configure existing hash factors, or customize hash perturbation factors
|
Note: Because ECMP is a three-layer forwarding, even if the configuration is based on source MAC, destination MAC, or source-destination MAC as the HASH factor, the system will default to selecting the source IP as the HASH factor. In addition, when selecting to extract the HASH factor as the destination IP, the system will default to selecting the source-destination IP as the HASH factor.
Step 2: HASH calculation
There are many types of HASH algorithms. We will use the XOR algorithm as an example. The XOR algorithm rule includes that if the two input bits are the same, they are 0, and if they are different, they are 1. The HASH factors are different, and the operation results are also different.
1. HASH factor is IP address source (SIP)
2. HASH factor is SIP+DIP/DIP
3.HASH factor is SIP+DIP+SP+DP
Step 3: Confirm the next forwarding hop
The above process is the normal forwarding process of ECMP, but problems may occur during operation in a specific network environment. Next, we will continue to analyze two common problems encountered by ECMP in data center networks.
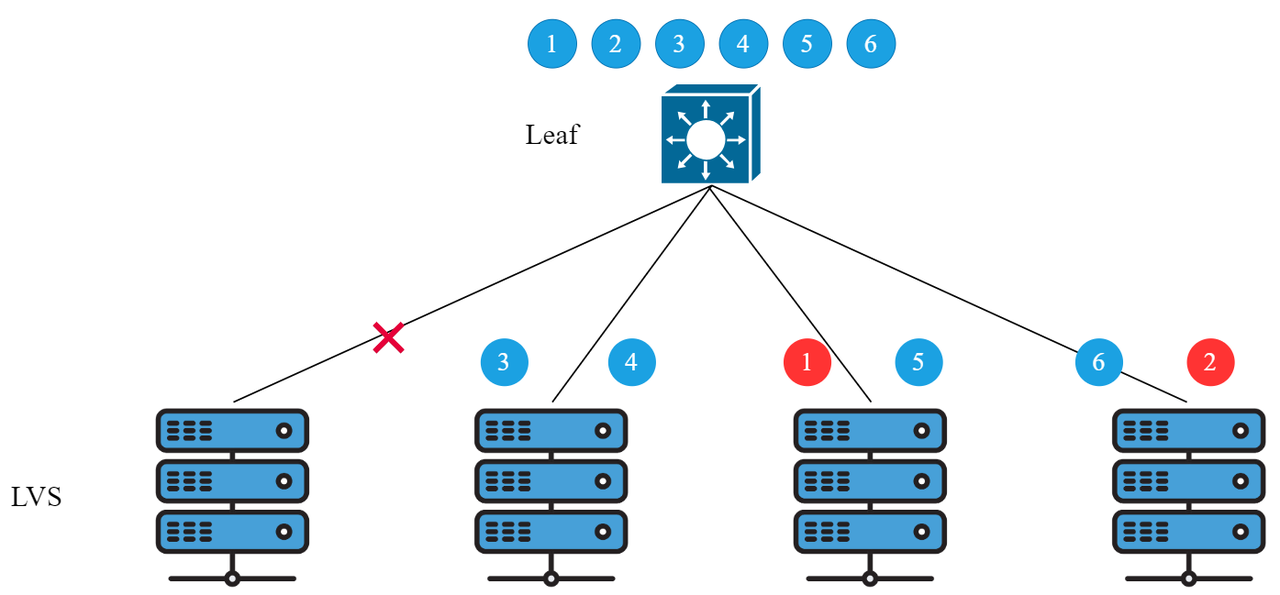
Problem 1: A single link failure causes all data flows in the ECMP group to be re-hashed
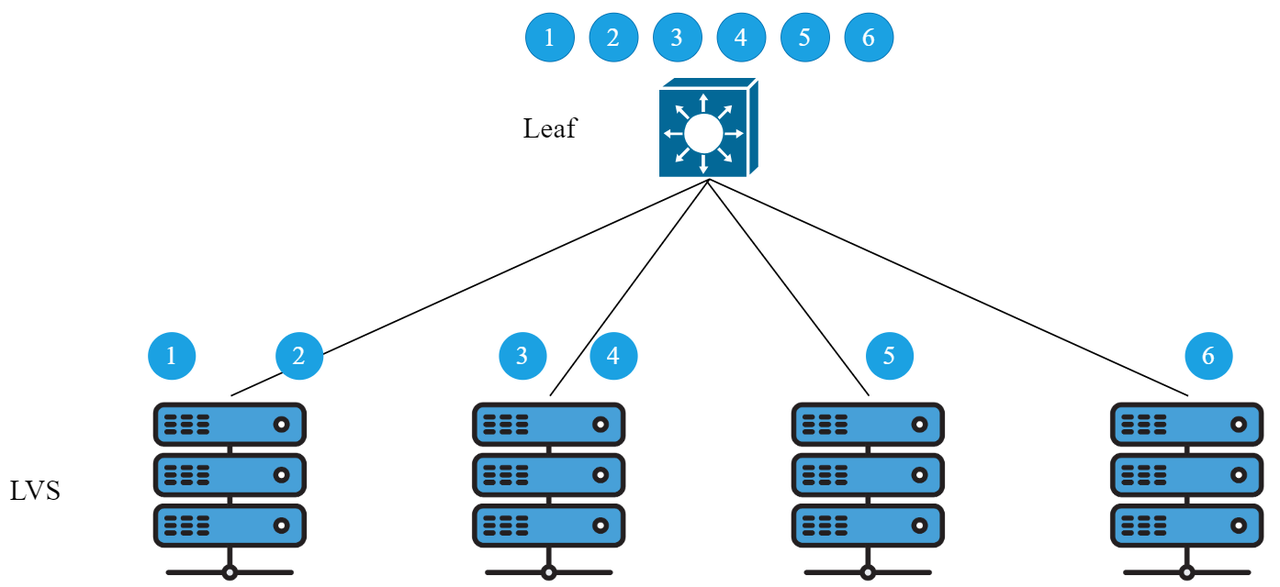
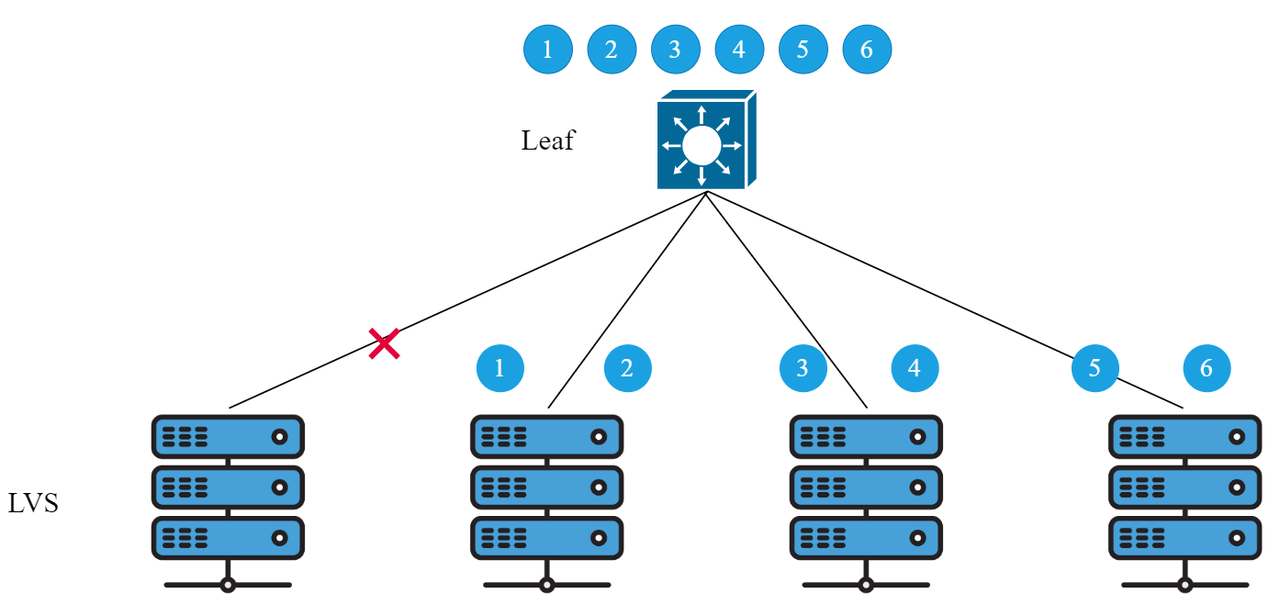
Optimization plan:
Specific implementation principle of elastic HASH:
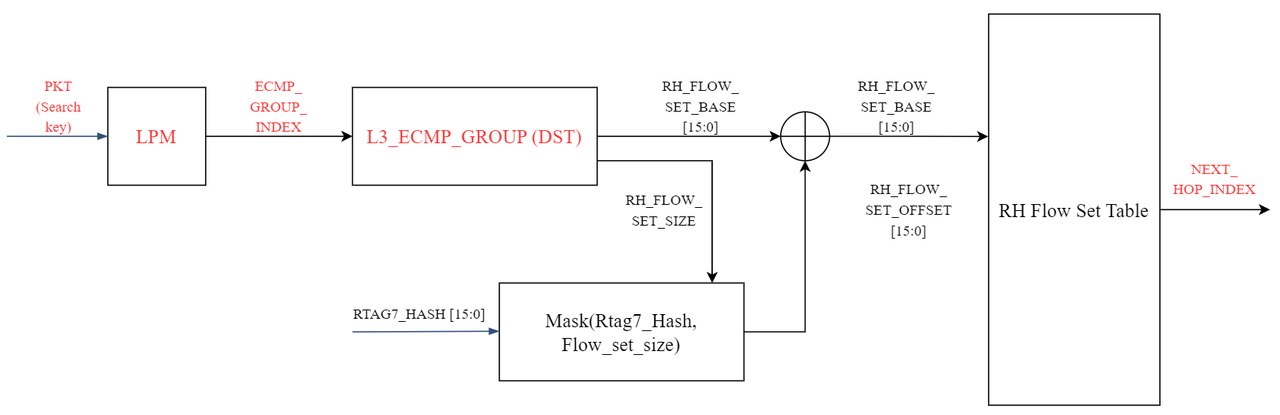
|
RH Flow Table
|
|
|
base PTR=0
|
flow-size=8
|
|
mod=1
|
Next hop=1
|
|
mod=2
|
Next hop=2
|
|
mod=1
|
Next hop=1
|
|
mod=4
|
Next hop=4
|
|
mod=1
|
Next hop=1
|
|
mod=2
|
Next hop=2
|
|
mod=2
|
Next hop=2
|
|
mod=4
|
Next hop=4
|
|
base PTR=8
|
flow-size=8
|
|
mod=5
|
Next hop=5
|
|
mod=6
|
Next hop=6
|
|
mod=7
|
Next hop=7
|
|
mod=8
|
Next hop=8
|
|
mod=5
|
Next hop=5
|
|
mod=6
|
Next hop=6
|
|
mod=7
|
Next hop=7
|
|
mod=8
|
Next hop=8
|
|
RH Flow Table
|
|
|
base PTR=0
|
flow-size=8
|
|
mod=1
|
Next hop=1
|
|
mod=2
|
Next hop=2
|
|
mod=3
|
Next hop=3
|
|
mod=4
|
Next hop=4
|
|
mod=1
|
Next hop=1
|
|
mod=2
|
Next hop=2
|
|
mod=3
|
Next hop=3
|
|
mod=4
|
Next hop=4
|
|
base PTR=8
|
flow-size=8
|
|
mod=5
|
Next hop=5
|
|
mod=6
|
Next hop=6
|
|
mod=7
|
Next hop=7
|
|
mod=8
|
Next hop=8
|
|
mod=5
|
Next hop=5
|
|
mod=6
|
Next hop=6
|
|
mod=7
|
Next hop=7
|
|
mod=8
|
Next hop=8
|
Problem 2: HASH polarization problem
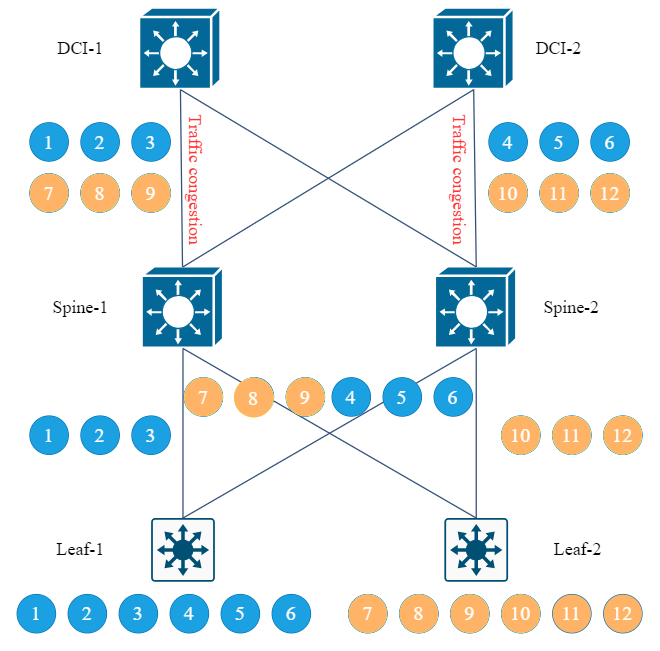
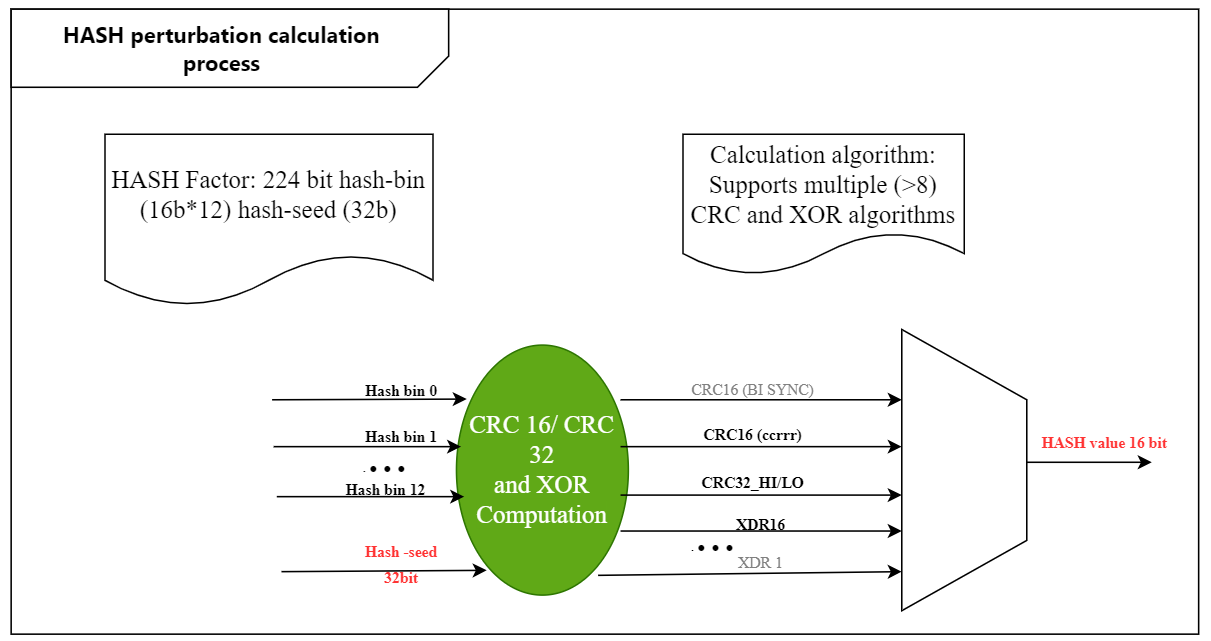
Optimization plan:
During the calculation of HASH disturbance, the HASH factor is still extracted normally, and then the user-defined random disturbance factor is added. After the HASH algorithm is calculated, the HASH calculation results of different switches will be inconsistent, so as to avoid the occurrence of HASH polarization.
Implementation of Dynamic Load Balancing Technology
Ruijie Networks' next-generation 25G data center network solution the new chip can support the DLB (Dynamic load balance) feature, which can realize dynamic HASH load balancing based on the traffic load status. The specific implementation method is that the switch creates a flow table for each data flow to be load balanced, records traffic statistics based on the flow table and dynamically adjusts the link load balancing according to the traffic statistics.
Summary
Related Blog:
Exploration of Data Center Automated Operation and Maintenance Technology: Zero Configuration of Switches
Technology Feast | How to De-Stack Data Center Network Architecture
Technology Feast | A Brief Discussion on 100G Optical Modules in Data Centers
Featured blogs
- Ruijie RALB Technology: Revolutionizing Data Center Network Congestion with Advanced Load Balancing
- CXL 3.0: Solving New Memory Problems in Data Centres (Part 2)
- Multi-Tenant Isolation Technology in AIGC Networks—Data Security and Performance Stability
- Multi-dimensional Comparison and Analysis of AIGC Network Card Dual Uplink Technical Architecture
- A Brief Discussion on the Technical Advantages of the LPO Module in the AIGC Computing Power Network











