Software Specifications |
RG-AP180(V3) |
| Basic Function |
| Applicable software version |
RGOS11.9(6)B9 or later |
| WLAN |
| Maximum number of associated STAs |
256 (up to 128 STAs per radio) |
| Practical maximum client count indication (per device) |
128 |
| Maximum number of BSSIDs |
16 (up to 8 BSSIDs per radio) |
| Maximum number of WLAN IDs |
8 |
| STA management |
SSID hiding Band steering Each SSID can be configured with the authentication mode, encryption mechanism, and VLAN attributes independently. Remote Intelligent Perception Technology (RIPT) Intelligent STA identification technology Intelligent load balancing based on the STA quantity or traffic Rate set settings |
| STA limiting |
SSID-based STA limiting Radio-based STA limiting |
| Bandwidth limiting |
STA/SSID/AP-based rate limiting |
| CAPWAP |
IPv4/IPv6 CAPWAP Layer 2 and Layer 3 topology between an AP and an AC An AP can automatically discover the accessible AC. An AP can be automatically upgraded through the AC. An AP can automatically download the configuration file from the AC. CAPWAP through NAT MTU setting and fragmentation over CAPWAP tunnels Encryption over CAPWAP data channels Encryption over CAPWAP control channels |
| Data forwarding |
Centralized and local forwarding |
| Wireless roaming |
Layer 2 and Layer 3 roaming |
| Wireless locating |
MU and TAG device locating |
| Security and Authentication |
| Authentication and encryption |
Remote Authentication Dial-In User Service (RADIUS) PSK, UPSK and web authentication QR code-based guest authentication, SMS authentication, and MAC address bypass (MAB) authentication Data encryption: WEP (64/128 bits), WPA (TKIP), WPA-PSK, WPA2 (AES), WPA3-Enterprise, WPA3-Individual |
| Data frame filtering |
Allowlist, static blocklist, and dynamic blocklist VLAN-based user isolation |
| WIDS |
Wireless Intrusion Detection System(WIDS) Wireless Intrusion Protection System(WIPS) User isolation Rogue AP detection and containment |
| Dynamic Policy |
IP standard ACL, MAC extended ACL, IP extended ACL, and expert-level ACL Time range-based ACL ACL based on a Layer 2 interface ACL based on a Layer 3 interface Ingress ACL based on a wireless interface Dynamic ACL assignment based on 802.1X authentication (used with the AC) CoA/DM |
| CPP |
CPU Protect Policy (CPP) |
| NFPP |
Network Foundation Protection Policy (NFPP) |
| Routing and Switching |
| MAC |
Static and filtered MAC addresses MAC address table size: 1,024 Maximum number of static MAC addresses: 1,024 Maximum number of filtered MAC addresses: 1,024 |
| Ethernet |
Jumbo frame length: 1,518 Full-duplex and half-duplex modes of interfaces IEEE802.1p and IEEE802.1Q |
| VLAN |
Interface-based VLAN assignment Maximum number of VLANs: 4,094 VLAN ID range: 1–4,094 |
| ARP |
ARP entry aging and proxy ARP Maximum number of ARP entries: 1,024 ARP check |
| IPv4 services |
Static and DHCP-assigned IPv4 addresses Maximum number of IPv4 addresses configured on each Layer 3 interface: 200 NAT, FTP ALG and DNS ALG |
| IPv6 services |
IPv6 addressing, Neighbor Discovery (ND), ICMPv6, IPv6 ping IPv6 DHCP client |
| IP routing |
IPv4/IPv6 static route Maximum number of static IPv4 routes: 1,024 Maximum number of static IPv6 routes: 1,000 |
| Multicast |
Multicast-to-unicast conversion |
| VPN |
PPPoE client IPsec VPN |
| Network Management and Monitoring |
| Network management |
NTP server and NTP client SNTP client SNMPv1/v2c/v3 Fault detection and alarm Information statistics and logging |
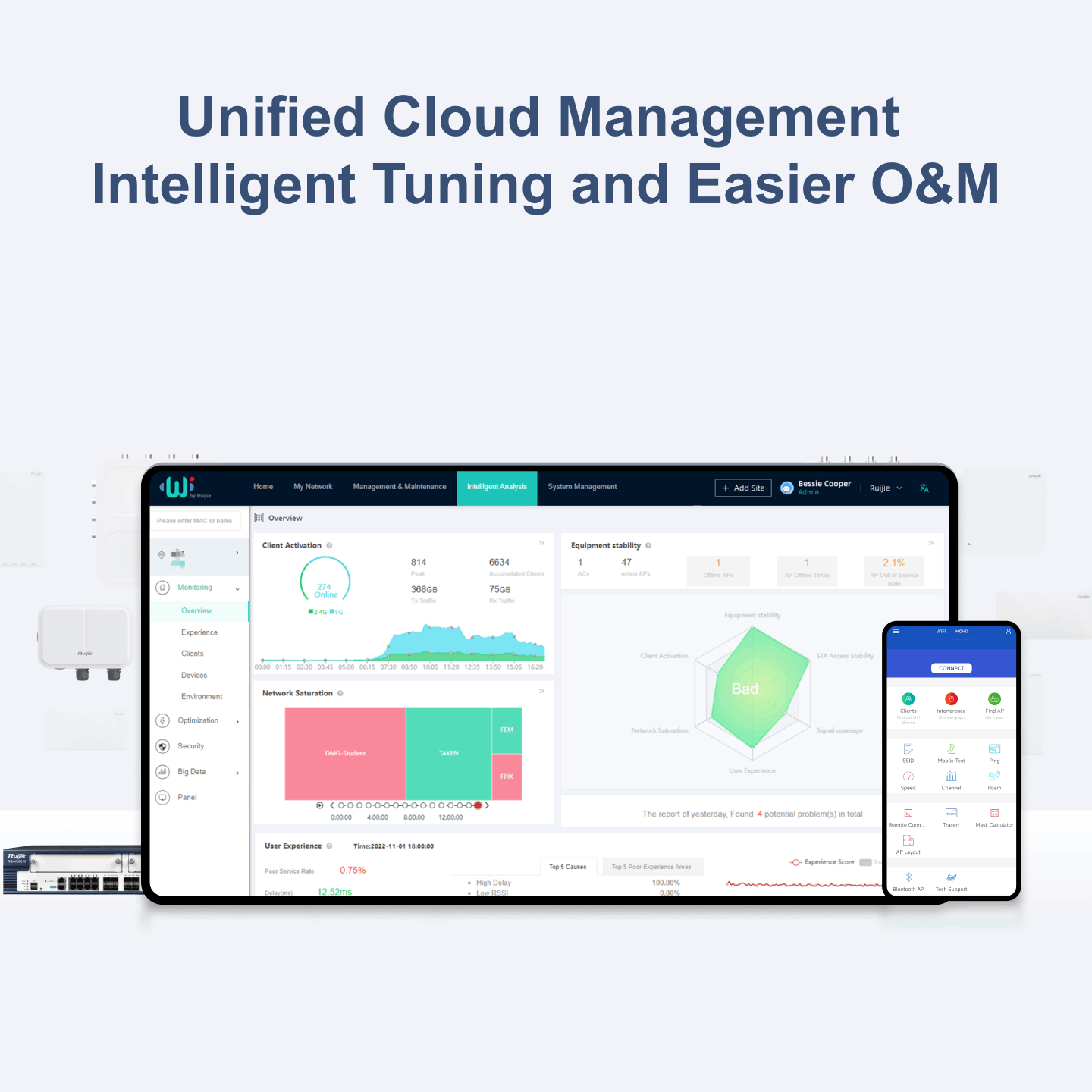
| Network management platform |
Web management (Eweb) |
| User access management |
Console, Telnet, and TFTP client Management |
| Switchover among Fat, Fit, and cloud modes |
When the AP works in Fit mode, it can be switched to Fat mode through an AC. When the AP works in Fat mode, it can be switched to Fit mode through the console port or Telnet mode. When the AP works in cloud mode, it can be managed through Ruijie Cloud. |